Not all MFA is created equal
Despite the growing tide and sophistication of cyber attacks, organizations continue to rely on legacy authentication methods such as usernames and passwords and mobile-based authenticators to secure access to critical and sensitive applications and data. A recent Google Cloud report indicates that 50% of compromises of enterprise cloud environments in Q4 2022 could be attributed to weak passwords.
Organizations face mounting pressure from regulators and cyber insurers to strengthen cybersecurity defenses with multi-factor authentication (MFA), adding one or more additional pieces of evidence to the authentication process. However, while any form of MFA will offer better security than password-based authentication alone, the truth is that not all MFA is created equal.
Legacy mobile-based MFA such as SMS, one-time passcodes (OTP) and push notification apps are highly susceptible to account takeovers from phishing, social engineering and man-in-the-middle (MiTM) attacks. And yet, up to 53% of or ganizations choose mobile-based authentication as their MFA form factor.2 Why is that? Because most organizations remain unaware of the security risks with mobile authentication.
Today a data breach costs an average of $9.44M in the US and $4.35M globally3, but cyber attacks can also erode trust, disable critical infrastructure, disrupt core operations, increase cyber insurance premiums and result in the loss of intellectual property. Successful cyber attacks are the reason why regulators now specifically mandate phishing-resistant MFA, including the White House Executive Order 140284, Office of Management and Budget (OMB) Memo 22-095 and the National Security Memorandum/NSM-86 in the US, NIS27 for the EU and the global PCI DSS v4.0 standard8. And yet across the industry, confusion still exists about what forms of MFA are truly secure or phishing-resistant.
The dark truth is that no form of mobile authentication is phishing-resistant. Further, your MFA strategy ROI can vary widely in terms of cost, user experience, coverage and even the ability to bridge to a passwordless future, depending on what MFA approach you choose.
In this whitepaper, we’ll reveal the top five mobile authentication misconceptions to help you re-evaluate your long-term MFA strategy and to consider the shift to modern MFA. In fact, we’ll demonstrate that legacy mobile-based MFA is broken, and how you can achieve modern, phishing-resistant MFA with an estimated ROI as high as 203%.

Common forms of mobile authentication
The most common forms of mobile authentication rely on the human element—the manual entry of an output (code) or the approval of a sign-in request. The human element of authentication can have a direct impact on security risk, user productivity and support costs if the solution doesn’t offer an optimal user experience. In fact, 82% of data breaches can be tied to the human element—social attacks, credential theft, misuse or errors.
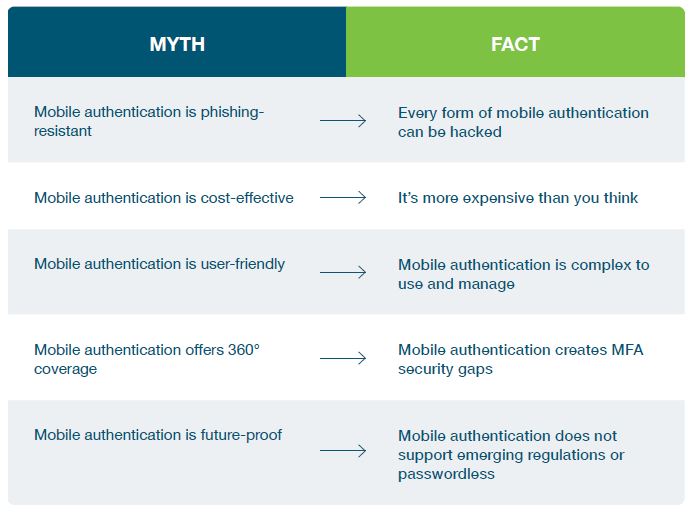
Five common misconceptions related to mobile authentication
Here are the top five mobile authentication misconceptions that put organizations at risk of account takeovers and increased OpEx and CapEx costs, if not addressed:
- #1: Mobile authentication is phishing-resistant
- #2: Mobile authentication is cost-effective
- #3: Mobile authentication is user-friendly
- #4: Mobile authentication offers 360° coverage
- #5: Mobile authentication is future-proofed
Yubikey offers simple, phishingresistant MFA
Yubico created the YubiKey, a hardware security key that supports phishing-resistant two-factor, MFA and passwordless authentication at scale with an optimized user experience.
The YubiKey is a multi-protocol key, supporting both PIV/smart card and FIDO2/WebAuthn standards along with OTP and OpenPGP, integrating seamlessly into both legacy and modern environments, helping organizations bridge to a passwordless future supported by hardware-bound passkeys.
Modern hardware security keys such as the YubiKey provide an authentication process that is free of human error, offering organizations a path to zero trust that is proven to reduce risk by 99.9%. The YubiKey works across the organization and in places legacy MFA can’t, free from reliance on external power, batteries or network connection.
The YubiKey is designed to deliver a great user experience, letting users securely log in to over one thousand products, services and applications, including leading identity and access management (IAM) platforms, privileged access management (PAM) solutions and cloud services, with the secrets never shared between services.
Getting started is easy
Net Universe has been recognized as the Yubico Strategic Partner of 2022. This award is a testament to our ongoing commitment to delivering the best security solutions to our clients.
Combining IT and logistics services, Net Universe is the unique YubiKey authorized distributor that has the ability to distribute or collect equipment anywhere in the world, without customs barriers, at the best cost and in times that no one can overcome.
If you need the best conditions to purchase Yubico products and licenses please visit our shop.
If you want to learn about our Yubico solutions with integrated logistics services, taking your company to the next level, please make an appoinment with a specialist.




