Customer Perspectives
An organization’s continued growth depends on their vision and roadmap to expand business opportunities, and this is especially true in the financial services industry. And with expansion, comes the immediate need to implement solutions that meet the demands of business-critical applications rapidly shifting to the cloud, while preserving a strong security posture at all edges. Organizations have understood the cost effectiveness of moving away from MPLS to cheaper and more effective alternatives such as broadband and LTE for some time now, but this has not exactly solved the problem of achieving the best user experience with visibility and control into their network performance.
Large distributed enterprises with thousands of branch offices need reliable and secure connectivity from home to branch to data center to cloud. There is an urgent need for digital innovation to address challenges such as a lack of centralized control, poor real-time application performance with traditional routing technologies, and security. They require quick deployment and change management enabled with automation to translate their business intent to effective business policies and deliver exceptional application performance while maintaining business continuity.
With a single dedicated WAN link at every one of their 3,000 branch locations, one large financial services organization began experiencing poor application performance that had a severe impact on their workforce and customer experience with business-critical financial applications. Security measures for centralized inspection and cloud access were implemented in their data centers, which forced branch traffic to be backhauled. These factors put tremendous strain on bandwidth and performance across their dedicated MPLS circuits, and the clear solution was to move away from MPLS to multiple direct internet access with a secure, reliable, and consolidated WAN Edge. Consolidation also meant complete visibility into all their applications, improved network performance that extends to branch/LAN networks for easy management and troubleshooting while also simplifying the network infrastructure, reduced OPEX + CAPEX costs, and accelerated cloud access.
Financial Service Organization Expands Business Opportunities
With several SD-WAN vendors vying for selection as part of their proof of concept trials, this organization was quick to discover that Fortinet’s robust Secure SD-WAN solution differentiated itself by providing a fully integrated solution that combined business agility, optimal connectivity, strong security, and best user experience into a single form factor that was easy to deploy and manage. Fortinet Secure SD-WAN is also able to provide WAN Edge consolidation with integrated self-healing SD-WAN and security on the industry’s best-performing appliance and centralized management extending to the branch network. Fortinet was the only solution that proved this organization could replace their legacy routers, poorly performing security solutions, and MPLS circuits with a single vendor to solve their infrastructure needs to ensure business continuity, improve application performance, and simplify branch management.
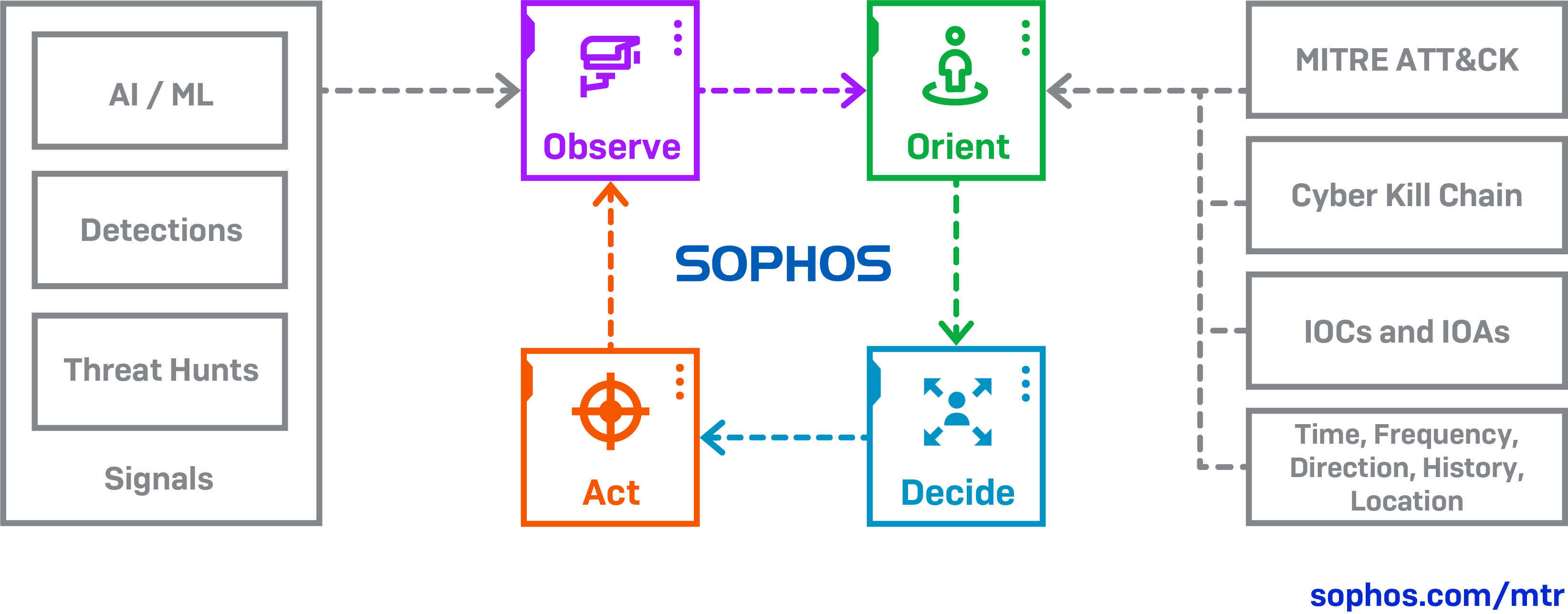
Key Benefits of Fortinet Secure SD-WAN
A few of the key benefits and immediate business outcomes provided by Fortinet’s Secure SD-WAN solution include:
- Self-healing Capabilities to Achieve Exceptional User Experience: Fortinet Secure SD-WAN solved their need for traffic steering based on application policy and network SLA such as packet loss, jitter, and latency to achieve best user experience for their business applications designed to handle critical customer financial transactions. With a compact desktop form factor offered with the FortiGate 50E series, they were able to replace MPLS circuits with dual high bandwidth broadband circuits that can effectively forward traffic in an active-active fashion and transform their infrastructure to self-heal with SD-WAN remediation capabilities and deliver optimal application performance across all branch offices.
- Reliable Connectivity for Business Continuity: This organization required reliable connectivity for their real-time application traffic, used extensively for companywide collaboration and customer service. Fortinet Secure SD-WAN’s ability to enable branch-to-branch VPN connectivity at scale and detect SLAs ensured the voice/video traffic were forwarded on the best available, highest performing, and lowest latency path to achieve best quality of experience.
- Cloud On-Ramp for Accelerated Cloud Access: They also required secure cloud access for compute and business applications hosted on AWS across their branch offices. Fortinet’s integrated NGFW and one touch connectivity to AWS virtual WANs enabled accelerated access to critical business applications on direct internet links, while ensuring a strong security posture.
- Ease of Management with Consolidation and Simplification from the WAN to LAN Edge: Prior to implementation, this organization experienced longer troubleshooting cycles due to limited visibility into their LAN and applications during their network outages. This also meant significant delays for their customer transactions, support and services. Fortinet’s centralized management and control offered with FortiManager enabled their IT staff to handle change management from WAN to LAN in a matter of days. Advanced analytics and telemetry offered both in real-time and historical via FortiAnalyzer allowed quick resolution cycles and IT staff to spend more cycles on digital innovations.
- Leveraging Fortinet Secure SD-Branch to Ensure Branch Office Security Without Impeding Productivity: By implementing Fortinet Secure SD-Branch at their remote locations, this organization gained complete visibility and control across their entire digital attack surface and was able to extend the benefits of the Fortinet Security Fabric to their distributed branch locations. Further, with branch-to-branch VPN connectivity at scale, this financial service organization enabled secure connectivity without impeding productivity for employees.
Take a security-driven approach to networking to improve user experience and simplify operations at the WAN edge with Fortinet’s Secure SD-WAN solution.
Read these customer case studies to see how De Heus and Burger King Brazil implemented Fortinet’s Secure SD-WAN to alleviate network complexity, increase bandwidth, and reduce security costs.
Engage in our Fortinet user community (Fuse). Share ideas and feedback, learn more about our products and technology, or connect with peers.
As Fortinet partners, Net Universe offers all Fortinet devices and subscriptions with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/fortinet.
You can visit our Shop Online