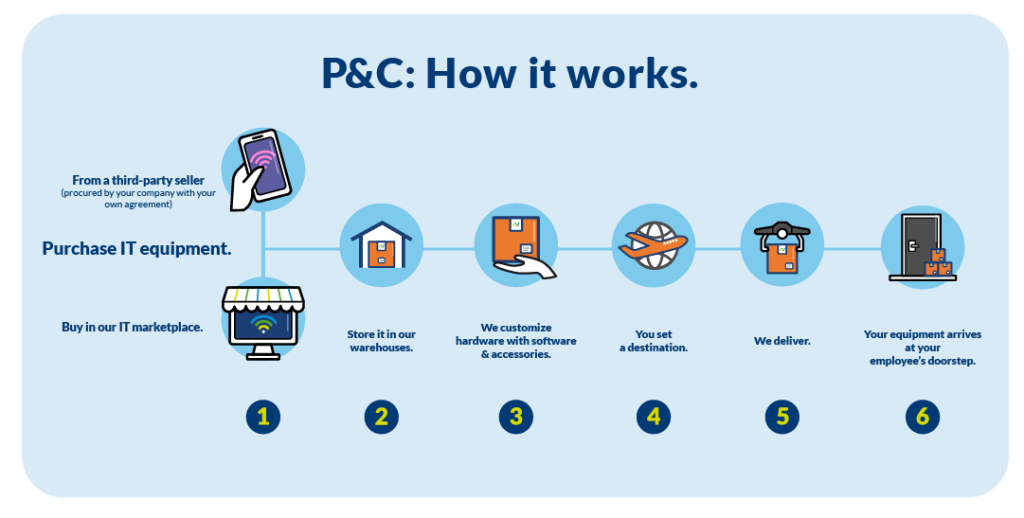
In the era of remote work, the speed and efficiency of delivering essential IT equipment has become a cornerstone of successful business operations. Through its Provision & Collection service, Net Universe ensures that organizations can receive IT equipment, such as laptops and keyboards, exactly where and when they need them, regardless of where their employees are located around the world.

Streamlined Delivery Logistics:
Net Universe has perfected its logistics process to ensure that each shipment, from a single device to thousands of units, reaches its destination safely and on time. We handle everything from gathering client requirements to the final delivery at the desired location, including all necessary customs procedures and tax barriers.
Case Study: Global Online Community Platform
A leading online community platform, with employees spread across more than 50 countries, faced the challenge of updating its IT hardware to meet the new demands of remote work. Through the Provision & Collection service by Net Universe, the company was able to coordinate the shipment of 600 laptops, each specifically configured for the end user’s needs. This process was carried out over a period of two months, covering regions in America, Europe, APAC, and EMEA. The efficiency and precision of the delivery allowed for a smooth and uninterrupted transition in the platform’s daily work, especially noted for its efficiency in locations with complex logistics such as Eastern European countries and South America.
Rapid Response for Immediate Needs:
We understand that time is critical. Our distribution model is designed to respond quickly to urgent requests, allowing businesses to maintain work continuity without costly delays, especially in locations with complex logistics like Eastern European countries, the Philippines, India, and South America.
Impact on Business Operations:
The effectiveness of our logistics not only simplifies IT management but also enhances employee satisfaction and efficiency. Properly configured and timely delivered equipment removes technical barriers, allowing workers to focus on their business objectives without distractions.
Conclusion:
Provision & Collection by Net Universe does not just deliver IT equipment; we facilitate the expansion and scalability of businesses with logistic solutions that exceed expectations. No matter where your employees are located, we guarantee they will have the necessary resources to perform at their best. Discover how we can help you simplify your remote IT management and boost your global business.
About Net Universe
Net Universe is the first Technology company with integrated Global Logistics.
With strategic alliances and partnerships with the main technology brands in equipment, security and collaboration platforms, Net Universe combines IT and logistics, delivering technology product and services with integrated logistics solutions, woldwide.
Contact us for more information: [email protected]
Schedule a meeting
Visit www.netuniversecorp.com