SASE (Secure Access Service Edge) has become a topic of increased industry discussion and interest for enterprises and partners alike. That’s because today’s organizations require immediate, uninterrupted, and secure access to network and cloud-based resources and data – especially business-critical applications – no matter where their users are located.
Digital innovation creates new challenges for organizations, including dynamically changing network configurations and the rapid expansion of the attack surface. This has resulted in new and incremental opportunities to provide additional levels of protection and access control that these organizations and users require. These are challenges that a SASE solution is designed to address.
However, there are two critical things to remember about the selection and implementation of any SASE solution. The first is that it must be easily integrated into your larger security strategy. If not, you are simply creating yet another set of stand-alone security solutions that require additional attention and resources. The second is that any SASE solution must not only meet current access and flexibility needs, but it must also support a Security-driven Networking strategy so it can quickly and automatically adapt to new network changes and evolving business requirements as they occur while providing robust, continuously-improved security and performance.
Fortinet Delivers the Most Complete SASE Platform on the Market
Because of the broad range of technologies it encompasses, and the variety of environments it needs to support, SASE is not a one-size-fits all secure access solution. Organizations have unique needs, and they need to be able to select and deploy those security offerings that are best-suited to their unique network environments and business requirements.
And yet, for SASE to work well, all of its components still need to interoperate as a single integrated system – connectivity, networking, and security elements alike. Part of the reason that sounds so familiar to us at Fortinet is that we have been delivering the core SASE requirements—plus much more—for years as part of our integrated Security Platform and Security Fabric architecture. A number of our customers looking to understand SASE have found that, with minor adjustments, they already had a SASE solution in place thanks to the power of the Security Fabric.
And now, to expand on the SASE flexibility and functionality already provided to customers and partners, Fortinet today announced the acquisition of OPAQ Networks, a SASE cloud provider. OPAQ’s Zero Trust Network Access (ZTNA) cloud solution protects organizations’ distributed networks – from data centers to branch offices, remote users, and Internet of Things (IoT) devices.
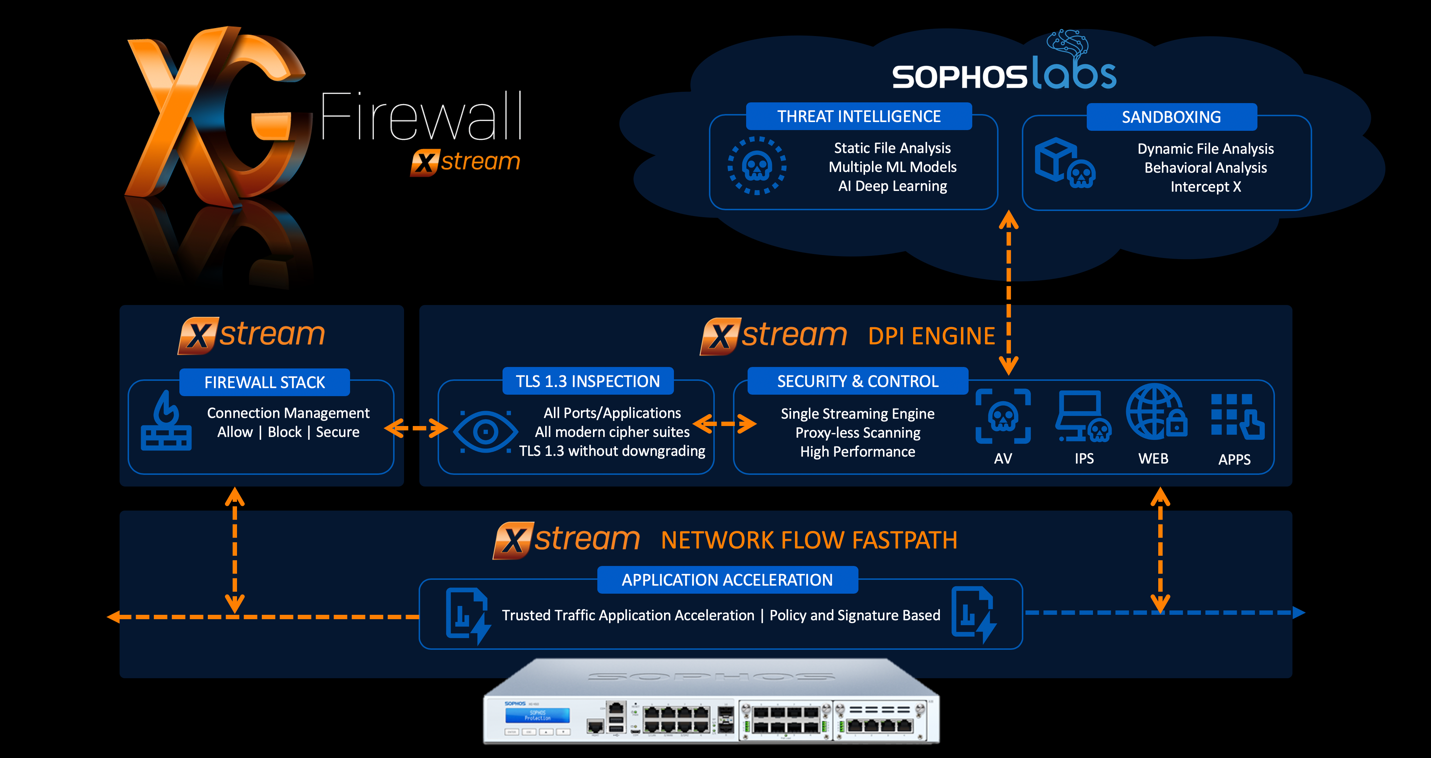
By combining Fortinet’s Security Fabric with OPAQ’s patented ZTNA solution, Fortinet further enhances its existing SASE offering to offer the best-in-class SASE cloud security platform with the industry’s only true Zero Trust access and security solution. It does this by integrating industry-leading next-generation firewall and SD-WAN capabilities, web security, sandboxing, advanced endpoint, identity / multi factor authentication, multi-cloud workload protection, cloud application security broker (CASB), browser isolation, and web application firewalling capabilities with a patented zero-trust cloud architecture to offer a flexible and dynamic SASE solution that can be managed and controlled through a single interface.
And Fortinet has the R&D scale and focus to deliver continuous innovation, with the best and broadest security “under the hood.” Unlike other cloud providers, who are missing a strong security backbone or a scalable, high performance cloud architecture—or, in some cases, both—Fortinet delivers cloud security, with the security.
“The acquisition of OPAQ further enhances our existing SASE offering. Now, we will deliver the most complete SASE platform on the market with the broadest security offering, industry-leading SD-WAN, and advanced networking solutions to customers and partners through a flexible, cost efficient, and patented zero-trust cloud architecture,” shared Ken Xie, Founder, Chairman of the Board, and CEO of Fortinet.
Moreover, OPAQ’s platform is purpose-built to be partner friendly, empowering MSSPs, carriers, and high value-add partners to easily integrate its multi-tenant SASE platform into their own offering. This enables these service providers to add critical value to their business and government customers through their Network Operations Center and Security Operations Center expertise and advanced professional services.
Given remote workforce trends, with exponentially more users, devices, applications, services, and data now operating outside of the traditional enterprise edge than inside, the integration of Fortinet’s broad Security Fabric with OPAQ’s cloud platform offers customers and partners even more choices as to how they can consume best-of-breed security. And it is yet another unique and differentiated way that Fortinet is empowering customers with the best, and truly integrated security and networking innovation designed to respond to evolving business needs in real-time.
Fortinet Enhances SASE and ZTNA Offerings with Cloud Delivery Enhanced Capabilities
With the OPAQ acquisition, unlike other cloud security providers, Fortinet delivers:
- The best of scalability, performance, and security compared to any cloud security vendor.
- A broad and integrated suite of cloud security solutions providing true Zero-Trust security, unlike other ZTNA providers who leave many unprotected gaps in the attack surface.
- A one-of-a-kind ZTNA solution that includes continuous security innovation at scale, leveraging Fortinet’s market-leading R&D talent to deliver security substance “under the hood.”
- The most partner-friendly ZTNA offering in the market that remains true to Fortinet’s ongoing commitment to its value-add services partners.
- Fully integrated security and networking, including Fortinet’s industry-leading SD-WAN, furthering the company’s Security-driven Networking approach.
To that last point, Xie added, “The recent SASE market momentum further validates our Security-driven Networking approach and underscores what we’ve been saying for years. In the current era of hyper connectivity and expanding networks, with the network edge stretching across the entire digital infrastructure, networking and security must converge.”
Today’s announcement of the integration of Fortinet’s broad and integrated security offerings with OPAQ’s SASE cloud platform delivers the most complete SASE platform on the market, enabling organizations to more rapidly and securely embrace digital innovation and compete more effectively in today’s digital marketplace.
Learn more about how Fortinet’s acquisiton of OPAQ Networks enhances its existing SASE offering, enabling Fortinet to deliver the most complete SASE platform on the market.