We’re a Magic Quadrant Leader! In Gartner’s recently published 2020 Magic Quadrant for WAN Edge Infrastructure, Fortinet has now been positioned in the Leader’s quadrant. We believe our commitment to continuous innovation helped Fortinet Secure SD-WAN place higher in ability to execute and further in completeness of vision.
Our SD-WAN journey began years ago, led with a security-driven networking approach that enabled us to deliver the industry’s first Secure SD-WAN solution. We have continued to innovate since then, delivering the world’s first purpose-built processor designed to accelerate SD-WAN functionality and security, while achieving a fully self-healing SD-WAN solution combined with centralized orchestration to meet the diverse needs of customers worldwide. Going forward we are excited to address additional emerging customer use-cases in the SD-WAN market with cloud-delivered SASE innovations to provide the most flexible secure access solution in the market.
The rapid adoption of cloud services and the current shift to remote workforce has accelerated the need for digital transformation. This has led customers worldwide to recognize the value of SD-WAN as they work to build a more robust WAN Infrastructure. While cost reduction, both in terms of operational overhead and capital expenditures, continues to influence the decision-making process, customers are also highly focused on application performance. Delivering business-critical services and cloud resources in real-time ensures the best possible user experience. When combined with the assurance of secure access from anywhere – whether from home or branch offices, or across multi-cloud environments – Fortinet Secure SD-WAN delivers a complete solution worthy of being designated as an industry leader.
Evolving cloud applications poses a significant challenge to steering decisions made by SD-WAN solutions, which can have adverse effects on application performance. By combining the industry’s best performance with advanced remediation techniques, such as dynamic traffic steering, forward error correction, and packet duplication, Fortinet Secure SD-WAN can automatically repair complex WAN issues that can undermine network performance. Combined with Fortinet’s AI/ML-powered application learning, customers can establish advanced visibility and control at every edge to improve performance, expand business agility, and achieve higher levels of productivity to deliver and maintain a better application experience and drive growth and revenue further and faster.
Fortinet also provides one of the widest arrays of Secure SD-WAN solutions, allowing us to achieve an extensive presence across all market segments, from small retail to complex global WAN infrastructures. Part of our advantage is that by converging advanced networking and security into a unified Secure SD-WAN solution, customers are able to eliminate point products at the WAN edge to reduce cost and achieve consolidation, and for industry’s best TCO. Simplification through centralized SD-WAN orchestration also enables organizations to expedite deployment, thereby reducing complexity and associated staff hours spent on management and troubleshooting complex network issues. And its actionable analytics and reports empower IT staff to fine-tune business and security policy at scale, as well as ensure ease of change management because it enables networking and security staff to work as a unified team.
But SD-WAN is about much more than just secure connectivity for branch offices. With applications and workloads moving to cloud-delivered models, businesses need reliable and secure access at the cloud edge as well. Fortinet’s differentiated vision also enables customers to future-proof their digital transformation investments by extending SD-WAN to multi-cloud, providing flexible secure access for their remote workforce anytime and anywhere. In addition, close proximity to applications can also optimize SaaS connectivity and cloud compute. And innovations in Fortinet’s cloud orchestrator help organizations extend end-to-end visibility and control to all edges, whether devices are on or off-premises.
For 20 years, Fortinet – a recognized industry expert – has not only focused on security solutions. We also design and deliver a portfolio of advanced network and access devices that span the entire networking stack. These years of experience in building and delivering advanced routing functionalities are what led to our evolution as the industry’s first Secure SD-WAN vendor, providing robust connectivity and routing functionality combined with a full suite of advanced security.
Innovations in both security and networking, focused vision on flexible secure access from and to anywhere, and continuous industry recognition from a range of third-party organizations, has fueled our expansion across all business verticals, and we believe this has led to our placement as a Leader in Gartner’s 2020 Magic Quadrant for WAN Edge Infrastructure. We believe our proven track record of providing business agility across all verticals and industries just got much stronger. And it doesn’t stop there. We have several upcoming announcements that will ensure that our Secure SD-WAN solution can address the broadest set of customer deployments – because being a leader never means standing in one place.
Gartner Magic Quadrant for WAN Edge Infrastructure, Jonathan Forest, Mike Toussaint, Mark Fabbi, September 2020
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Fortinet.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Download the full Gartner Magic Quadrant for WAN Edge Infrastructure report here.
Learn how Fortinet’s Secure SD-WAN Solution uses a security-driven networking approach to improve user experience and simplify operations at the WAN Edge.
As Fortinet partners, Net Universe offers all Fortinet devices and subscriptions with worldwide Delivery Services.
Send us an email to [email protected] for more information or visit https://www.netuniversecorp.com/fortinet.
You can visit our Shop Online









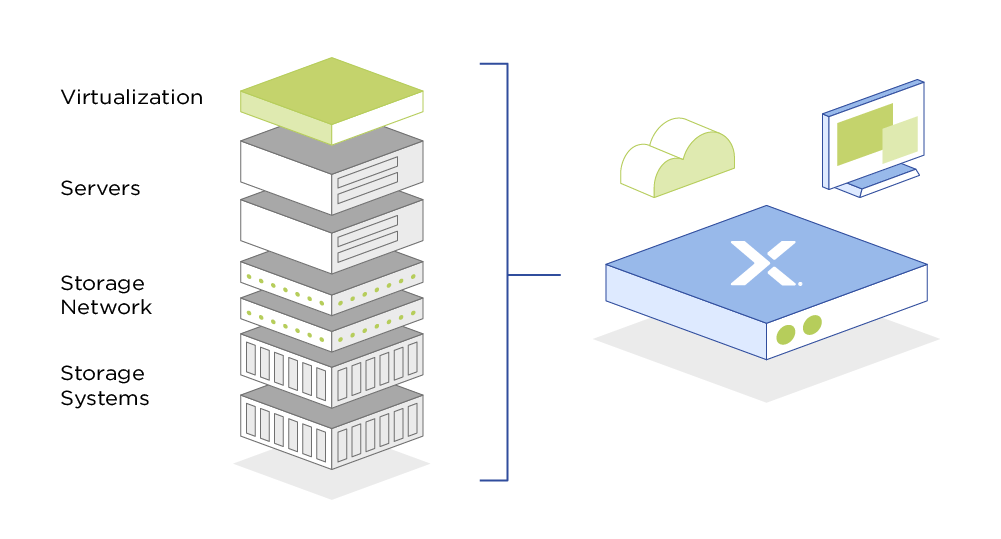
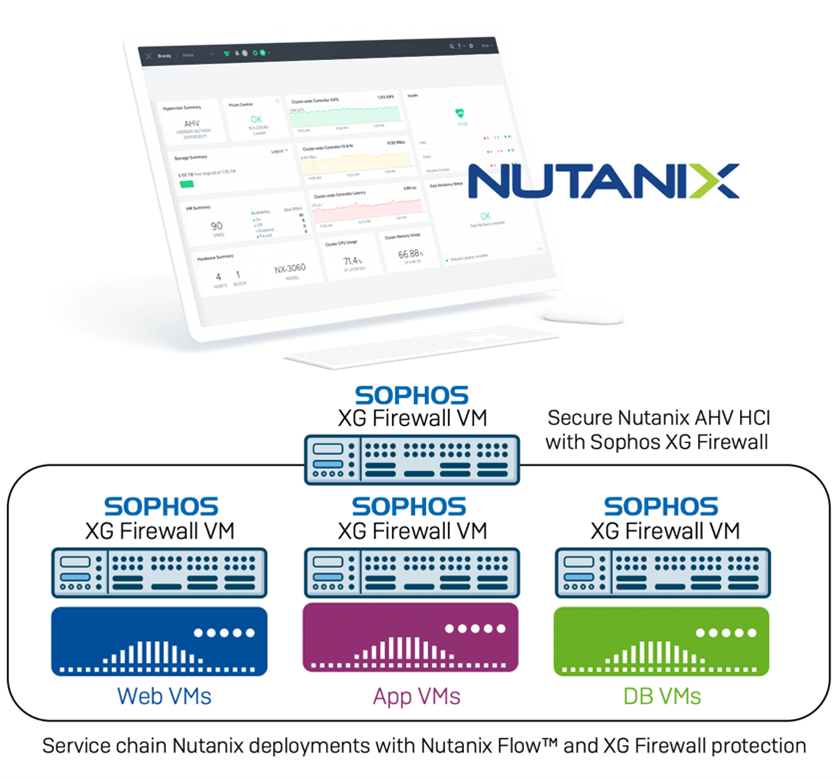
 Sophos XG Firewall has joined the robust and growing Nutanix ecosystem that is enabling global enterprises to converge and virtualize their IT infrastructure.
Sophos XG Firewall has joined the robust and growing Nutanix ecosystem that is enabling global enterprises to converge and virtualize their IT infrastructure.